|
Central Data Service |
||
|
Online Teaching | ||
|
Email : [email protected] (44) (0) 7943055280 |
||
Characteristics of the OSI Model
Here are some important characteristics of the OSI model:
A layer should only be created where the definite levels of abstraction are needed.
The function of each layer should be selected as per the internationally standardised protocols.
The number of layers should be large so that separate functions should not be put in the same layer. At the same time, it should be small enough so that architecture doesn’t become very complicated.
In the OSI model, each layer relies on the next lower layer to perform primitive functions. Every level should able to provide services to the next higher layer
Changes made in one layer should not need changes in other lavers.
Why the OSI Model?
Helps you to understand communication over a network
Troubleshooting is easier by separating functions into different network layers.
Helps you to understand new technologies as they are developed.
Allows you to compare primary functional relationships on various network layers.
History of OSI Model
Here are essential landmarks from the history of OSI model:
In the late 1970s, the ISO conducted a program to develop general standards and methods of networking.
In 1973, an Experimental Packet Switched System in the UK identified the requirement for defining the higher-level protocols.
In the year 1983, OSI model was initially intended to be a detailed specification of actual interfaces.
0In 1984, the OSI architecture was formally adopted by ISO as an international standard
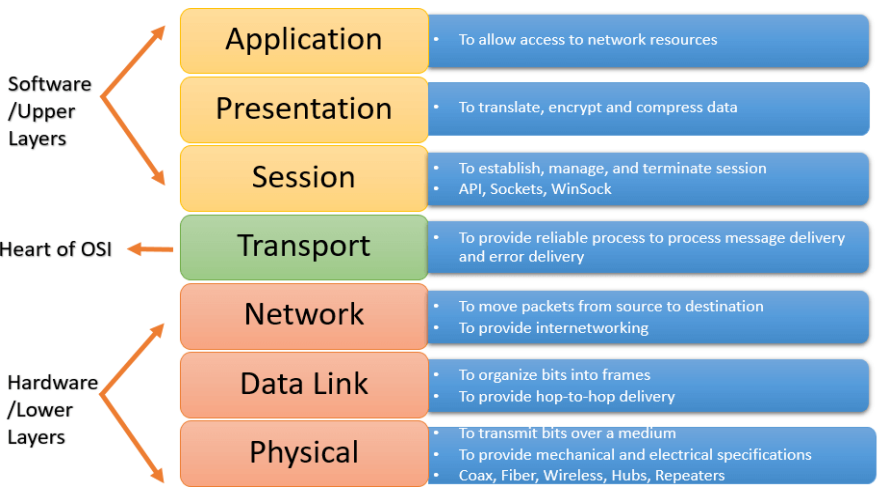
OSI model is a layered server architecture system in which each layer is defined according to a specific function to perform. All these seven layers work collaboratively to transmit the data from one layer to another.
The Upper Layers: It deals with application issues and mostly implemented only in software. The highest is closest to the end system user. In this layer, communication from one end-user to another begins by using the interaction between the application layer. It will process all the way to end-user.
The Lower Layers: These layers handle activities related to data transport. The physical layer and data link layers also implemented in software and hardware.
Upper and lower layers further divide network architecture into seven different layers as below:
Application
Presentation
Session
Transport
Network, Data-link
Physical layers

Physical Layer
The
physical layer helps you to define the electrical and physical
specifications of the data connection. This level establishes the
relationship between a device and a physical transmission medium. The
physical layer is not concerned with protocols or other such
higher-layer items.
Examples of hardware in the physical layer are
network adapters, ethernet, repeaters, networking hubs, etc
Data Link Layer
Data
link layer corrects errors which can occur at the physical layer. The
layer allows you to define the protocol to establish and terminates a
connection between two connected network devices.
It is IP address
understandable layer, which helps you to define logical addressing so
that any endpoint should be identified.
The layer also helps you
implement routing of packets through a network. It helps you to
define the best path, which allows you to take data from the source
to the destination.
The data link layer is subdivided into two
types of sublayers:
1.
Media Access Control (MAC) layer- It is responsible for controlling
how device in a network gain access to medium and permits to transmit
data.
2. Logical link control layer- This layer is responsible for
identity and encapsulating network-layer protocols and allows you to
find the error.
Important Functions of Data link Layer
Framing which divides the data from Network layer into frames.
Allows you to add header to the frame to define the physical address of the source and the destination machine
Adds Logical addresses of the sender and receivers
It is also responsible for the sourcing process to the destination process delivery of the entire message.
It also offers a system for error control in which it detects retransmits damage or lost frames.
Data link layer also provides a mechanism to transmit data over independent networks which are linked together.
Transport Layer
The
transport layer builds on the network layer to provide data transport
from a process on a source machine to a process on a destination
machine. It is hosted using single or multiple networks, and also
maintains the quality of service functions.
It determines how much
data should be sent where and at what rate. This layer builds on the
messages which are received from the application layer. It helps
ensure that data units are delivered error-free and in
sequence.
Transport layer helps you to control the reliability of
a link through flow control, error control, and segmentation or
desegmentation.
The transport layer also offers an acknowledgment
of the successful data transmission and sends the next data in case
no errors occurred. TCP is the best-known example of the transport
layer.
Important functions of Transport Layers
|
• |
It divides the
message received from the session layer into segments and numbers
them to |
Transport layer makes sure that the message is delivered to the correct process on the destination machine.
It also makes sure that the entire message arrives without any error else it should be retransmitted.
Network Layer
The
network layer provides the functional and procedural means of
transferring variable length data sequences from one node to another
connected in “different networks”.
Message delivery at
the network layer does not give any guaranteed to be reliable network
layer protocol.
Layer-management protocols that belong to the
network layer are:
1. routing protocols
2. multicast group
management
3. Network-layer addresses assignment.
Session Layer
Session Layer controls the dialogues between computers. It helps you to establish starting and terminating the connections between the local and remote application.
Important function of Session Layer
It establishes, maintains, and ends a session.
Session layer enables two systems to enter into a dialog
It also allows a process to add a checkpoint to steam of data.
Presentation Layer
Presentation
layer allows you to define the form in which the data is to exchange
between the two communicating entities. It also helps you to handles
data compression and data encryption.
This layer transforms data
into the form which is accepted by the application. It also formats
and encrypts data which should be sent across all the networks. This
layer is also known as a syntax layer.
The function of Presentation Layers
Character code translation from ASCII to EBCDIC.
Data compression: Allows reducing the number of bits that needs to be transmitted on the network.
Data encryption: Helps you to encrypt data for security purposes — for example, password encryption.
It provides a user interface and support for services like email and file transfer.
Application Layer
Application
layer interacts with an application program, which is the highest
level of OSI model.
The application layer is the OSI layer, which
is closest to the end-user. It means OSI application layer allows
users to interact with other software application.
Application
layer interacts with software applications to implement a
communicating component. The interpretation of data by the
application program is always outside the scope of the OSI
model.
Example of the application layer is an application such as
file transfer, email, remote login, etc.
The functions of the Application Layers are
Application-layer helps you to identify communication partners, determining resource availability, and synchronizing communication.
It allows users to log on to a remote host
This layer provides various e-mail services
This application offers distributed database sources and access for global information about various objects and services.
The physical layer helps you to define the electrical and physical specifications of the data connection. This level establishes the relationship between a device and a physical transmission medium. The physical layer is not concerned with protocols or other such higher-layer items.
Examples of hardware in the physical layer are network adapters, ethernet, repeaters, networking hubs, etc.
Data link layer corrects errors which can occur at the physical layer. The layer allows you to define the protocol to establish and terminates a connection between two connected network devices.
It is IP address understandable layer, which helps you to define logical addressing so that any endpoint should be identified.
The layer also helps you implement routing of packets through a network. It helps you to define the best path, which allows you to take data from the source to the destination.
The data link layer is subdivided into two types of sublayers:
Media Access Control (MAC) layer- It is responsible for controlling how device in a network gain access to medium and permits to transmit data.
Logical link control layer- This layer is responsible for identity and encapsulating network-layer protocols and allows you to find the error.
Framing which divides the data from Network layer into frames.
Allows you to add header to the frame to define the physical address of the source and the destination machine
Adds Logical addresses of the sender and receivers
It is also responsible for the sourcing process to the destination process delivery of the entire message.
It also offers a system for error control in which it detects retransmits damage or lost frames.
Datalink layer also provides a mechanism to transmit data over independent networks which are linked together.
The transport layer builds on the network layer to provide data transport from a process on a source machine to a process on a destination machine. It is hosted using single or multiple networks, and also maintains the quality of service functions.
It determines how much data should be sent where and at what rate. This layer builds on the message which are received from the application layer. It helps ensure that data units are delivered error-free and in sequence.
Transport layer helps you to control the reliability of a link through flow control, error control, and segmentation or desegmentation.
The transport layer also offers an acknowledgment of the successful data transmission and sends the next data in case no errors occurred. TCP is the best-known example of the transport layer.
It divides the message received from the session layer into segments and numbers them to make a sequence.
Transport layer makes sure that the message is delivered to the correct process on the destination machine.
It also makes sure that the entire message arrives without any error else it should be retransmitted.
The network layer provides the functional and procedural means of transferring variable length data sequences from one node to another connected in “different networks”.
Message delivery at the network layer does not give any guaranteed to be reliable network layer protocol.
Layer-management protocols that belong to the network layer are:
routing protocols
multicast group management
network-layer address assignment.
Session Layer controls the dialogues between computers. It helps you to establish starting and terminating the connections between the local and remote application.
This layer request for a logical connection which should be established on end user’s requirement. This layer handles all the important log-on or password validation.
Session layer offers services like dialog discipline, which can be duplex or half-duplex. It is mostly implemented in application environments that use remote procedure calls.
Important function of Session Layer:
It establishes, maintains, and ends a session.
Session layer enables two systems to enter into a dialog
It also allows a process to add a checkpoint to steam of data.
Presentation layer allows you to define the form in which the data is to exchange between the two communicating entities. It also helps you to handles data compression and data encryption.
This layer transforms data into the form which is accepted by the application. It also formats and encrypts data which should be sent across all the networks. This layer is also known as a syntax layer.
Character code translation from ASCII to EBCDIC.
Data compression: Allows to reduce the number of bits that needs to be transmitted on the network.
Data encryption: Helps you to encrypt data for security purposes — for example, password encryption.
It provides a user interface and support for services like email and file transfer.
Application layer interacts with an application program, which is the highest level of OSI model. The application layer is the OSI layer, which is closest to the end-user. It means OSI application layer allows users to interact with other software application.
Application layer interacts with software applications to implement a communicating component. The interpretation of data by the application program is always outside the scope of the OSI model.
Example of the application layer is an application such as file transfer, email, remote login, etc.
Application-layer helps you to identify communication partners, determining resource availability, and synchronizing communication.
It allows users to log on to a remote host
This layer provides various e-mail services
This application offers distributed database sources and access for global information about various objects and services.
Information sent from a one computer application to another needs to pass through each of the OSI layers.
This is explained in the below-given example:
Every layer within an OSI model communicates with the other two layers which are below it and its peer layer in some another networked computing system.
In the below-given diagram, you can see that the data link layer of the first system communicates with two layers, the network layer and the physical layer of the system. It also helps you to communicate with the data link layer of, the second system.
|
Layer |
Name |
Protocols |
|---|---|---|
|
Layer 7 |
Application |
SMTP, HTTP, FTP, POP3, SNMP, TELNET |
|
Layer 6 |
Presentation |
MPEG, ASCH, SSL, TLS |
|
Layer 5 |
Session |
NetBIOS, SAP, NFS |
|
Layer 4 |
Transport |
TCP, UDP, ICMP |
|
Layer 3 |
Network |
IPV4, IPV6, ICMP, IPSEC, ARP, MPLS. |
|
Layer 2 |
Data Link |
RAPA, PPP, Frame Relay, ATM, Fiber Cable, etc. |
|
Layer 1 |
Physical |
RS232, 100BaseTX, ISDN, 11. |
Here, are some important differences between the OSI & TCP/IP model:
|
OSI Model |
TCP/IP model |
|---|---|
|
OSI model provides a clear distinction between interfaces, services, and protocols. |
TCP/IP doesn’t offer any clear distinguishing points between services, interfaces, and protocols. |
|
OSI uses the network layer to define routing standards and protocols. |
TCP/IP uses only the Internet layer. |
|
OSI model use two separate layers physical and data link to define the functionality of the bottom layers |
TCP/IP uses only one layer (link). |
|
OSI model, the transport layer is only connection-oriented. |
A layer of the TCP/IP model is both connection-oriented and connectionless. |
|
In OSI model, data link layer and physical are separate layers. |
In TCP data link layer and physical layer are combined as a single host-to-network layer. |
|
The minimum sise of the OSI header is 5 bytes. |
Minimum header sise is 20 bytes. |
Here, are major benefits/pros of using the OSI model :
It helps you to standardise router, switch, motherboard, and other hardware
Reduces complexity and standardises interfaces
Facilitates modular engineering
Helps you to ensure interoperable technology
Helps you to accelerate the evolution
Protocols can be replaced by new protocols when technology changes.
Provide support for connection-oriented services as well as connectionless service.
It is a standard model in computer networking.
Supports connectionless and connection-oriented services.
Offers flexibility to adapt to various types of protocols
Here are some cons/ drawbacks of using OSI Model:
Fitting of protocols is a tedious task.
You can only use it as a reference model.
Doesn’t define any specific protocol.
In the OSI network layer model, some services are duplicated in many layers such as the transport and data link layers
Layers can’t work in parallel as each layer need to wait to obtain data from the previous layer.
The OSI Model is a logical and conceptual model that defines network communication which is used by systems open to interconnection and communication with other systems
In OSI model, layer should only be created where the definite levels of abstraction are needed.
OSI layer helps you to understand communication over a network
In 1984, the OSI architecture was formally adopted by ISO as an international standard
|
Layer |
Name |
Function |
Protocols |
|---|---|---|---|
|
Layer 7 |
Application |
To allow access to network resources. |
SMTP, HTTP, FTP, POP3, SNMP |
|
Layer 6 |
Presentation |
To translate, encrypt and compress data. |
MPEG, ASCH, SSL, TLS |
|
Layer 5 |
Session |
To establish, manage, and terminate the session |
NetBIOS, SAP |
|
Layer 4 |
Transport |
The transport layer builds on the network layer to provide data transport from a process on a source machine to a process on a destination machine. |
TCP, UDP |
|
Layer 3 |
Network |
To provide internetworking. To move packets from source to destination |
IPV5, IPV6, ICMP, IPSEC, ARP, MPLS. |
|
Layer 2 |
Data Link |
To organise bits into frames. To provide hop-to-hop delivery |
RAPA, PPP, Frame Relay, ATM, Fiber Cable, etc. |
|
Layer 1 |
Physical |
To transmit bits over a medium. To provide mechanical and electrical specifications |
RS232, 100BaseTX, ISDN, 11. |
Telephone network modems
IrDA physical layer
USB physical layer
Ethernet physical layer 10BASE-T, 10BASE2, 10BASE5, 100BASE-TX, 100BASE-FX, 1000BASE-T, 1000BASE-SX and other varieties
T1 and other T-carrier links, and E1 and other E-carrier links
ARINC 818 Avionics Digital Video Bus
CAN bus (controller area network) physical layer
Mobile Industry Processor Interface physical layer
Frame Relay
FO Fiber optics
ARCnet Attached Resource Computer NETwork
ARP Address Resolution Protocol
ATM Asynchronous Transfer Mode
CHAP Challenge Handshake Authentication Protocol
CDP Cisco Discovery Protocol
DCAP Data Link Switching Client Access Protocol
FDDI Fiber Distributed Data Interface
HDLC High-Level Data Link Control
IEEE 802.11 WiFi
IEEE 802.16 WiMAX
LACP Link Aggregation Control Protocol
L2F Layer 2 Forwarding Protocol
L2TP Layer 2 Tunneling Protocol
LLDP Link Layer Discovery Protocol
LLDP-MED Link Layer Discovery Protocol - Media Endpoint Discovery
MAC Media Access Control
Q.710 Simplified Message Transfer Part
Multi-link trunking Protocol
NDP Neighbor Discovery Protocol
PAgP - Cisco Systems proprietary link aggregation protocol
PPP Point-to-Point Protocol
PPTP Point-to-Point Tunneling Protocol
PAP Password Authentication Protocol
RPR IEEE 802.17 Resilient Packet Ring
SLIP Serial Line Internet Protocol (obsolete)
Space Data Link Protocol, one of the norms for Space Data Link from the Consultative Committee for Space Data Systems
STP Spanning Tree Protocol
Split multi-link trunking Protocol
Token Ring a protocol developed by IBM; the name can also be used to describe the token passing ring logical topology that it popularized.
Virtual Extended Network (VEN) a protocol developed by iQuila.
VTP VLAN Trunking Protocol
VLAN Virtual Local Area Network
IS-IS, Intermediate System - Intermediate System (OSI)
SPB Shortest Path Bridging
MTP Message Transfer Part
NSP Network Service Part
TRILL (TRansparent Interconnection of Lots of Links)
ARP Address Resolution Protocol
MPLS Multiprotocol Label Switching
PPPoE Point-to-Point Protocol over Ethernet
TIPC Transparent Inter-process Communication
CLNP Connectionless Networking Protocol
IPX Internetwork Packet Exchange
NAT Network Address Translation
SCCP Signalling Connection Control Part
AppleTalk DDP
HSRP Hot Standby Router protocol
VRRP Virtual Router Redundancy Protocol
ICMP Internet Control Message Protocol
ARP Address Resolution Protocol
RIP Routing Information Protocol (v1 and v2)
OSPF Open Shortest Path First (v1 and v2)
IPSEC IPsec
AEP AppleTalk Echo Protocol
AH Authentication Header over IP or IPSec
DCCP Datagram Congestion Control Protocol
ESP Encapsulating Security Payload over IP or IPSec
FCP Fibre Channel Protocol
NetBIOS NetBIOS, File Sharing and Name Resolution
iSCSI Internet Small Computer System Interface
NBF NetBIOS Frames protocol
SCTP Stream Control Transmission Protocol
Sinec H1 for telecontrol
TUP, Telephone User Part
SPX Sequenced Packet Exchange
NBP Name Binding Protocol {for AppleTalk}
This layer, presentation Layer and application layer are combined in TCP/IP model.
9P Distributed file system protocol developed originally as part of Plan 9
ADSP AppleTalk Data Stream Protocol
ASP AppleTalk Session Protocol
H.245 Call Control Protocol for Multimedia Communications
iSNS Internet Storage Name Service
NetBIOS, File Sharing and Name Resolution protocol - the basis of file sharing with Windows.
NetBEUI, NetBIOS Enhanced User Interface
NCP NetWare Core Protocol
PAP Printer Access Protocol
RPC Remote Procedure Call
RTCP RTP Control Protocol
SDP Sockets Direct Protocol
SMB Server Message Block
SMPP Short Message Peer-to-Peer
SOCKS "SOCKetS"
ZIP Zone Information Protocol {For AppleTalk}
This layer provides session management capabilities between hosts. For example, if some host needs a password verification for access and if credentials are provided then for that session password verification does not happen again. This layer can assist in synchronization, dialog control and critical operation management (e.g., an online bank transaction).
Independent Computing Architecture (ICA), the Citrix system core protocol
Lightweight Presentation Protocol (LPP)[2]
NetWare Core Protocol (NCP)
Network Data Representation (NDR)[2]
Tox, The Tox protocol is sometimes regarded as part of both the presentation and application layer
eXternal Data Representation (XDR)[2]
X.25 Packet Assembler/Disassembler Protocol (PAD)
SOAP, Simple Object Access Protocol
Simple Service Discovery Protocol, A discovery protocol employed by UPnP
TCAP, Transaction Capabilities Application Part
DHCP Dynamic Host Configuration Protocol
DNS Domain Name System
BOOTP Bootstrap Protocol
HTTP Hyper Text Transfer Protocol
POP3 Post Office Protocol
Telnet Tele Communication Protocol